Despite Oracle denying a breach of its Oracle Cloud federated SSO login servers and the theft of account data for 6 million people, BleepingComputer has confirmed with multiple companies that associated data samples shared by the threat actor are valid.
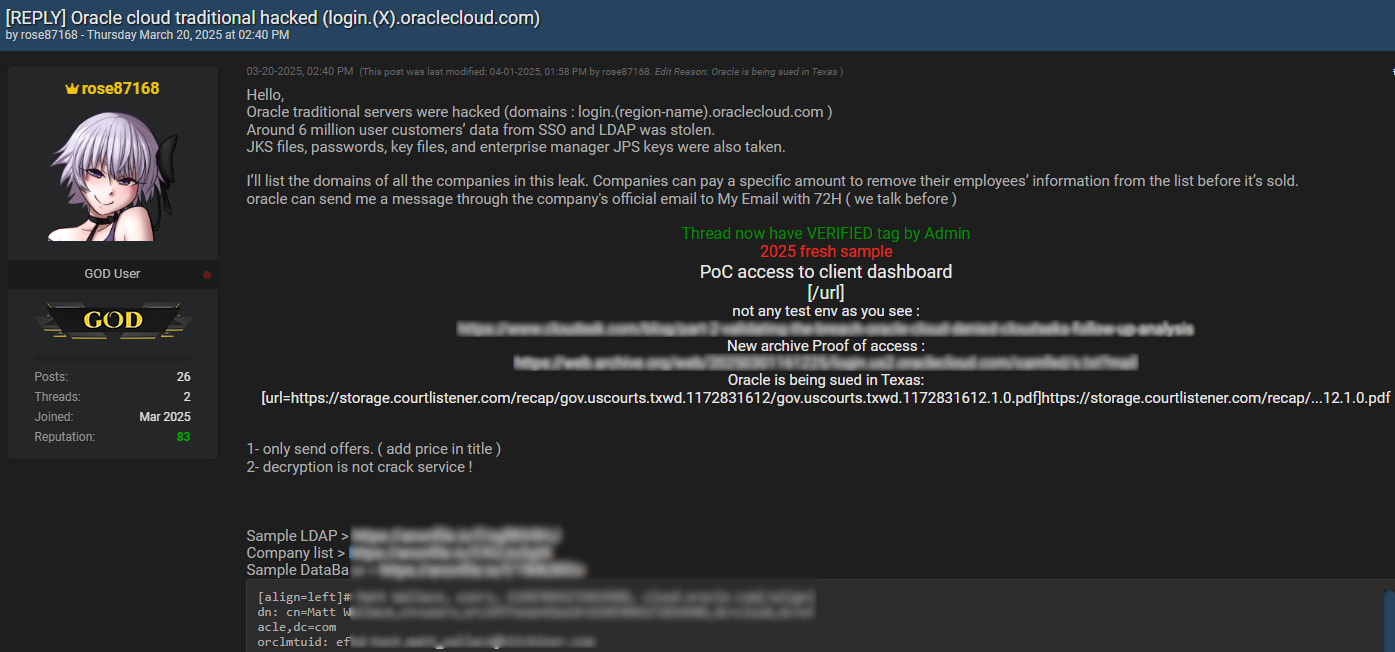
Last week, a person named ‘rose87168’ claimed to have breached Oracle Cloud servers and began selling the alleged authentication data and encrypted passwords of 6 million users. The threat actor also said that stolen SSO and LDAP passwords could be decrypted using the info in the stolen files and offered to share some of the data with anyone who could help recover them.
The threat actor released multiple text files consisting of a database, LDAP data, and a list of 140,621 domains for companies and government agencies that were allegedly impacted by the breach. It should be noted that some of the company domains look like tests, and there are multiple domains per company.
 Threat actor selling allegedly stolen Oracle Cloud data
Threat actor selling allegedly stolen Oracle Cloud data
Source: BleepingComputer
In addition to the data, rose87168 shared an Archive.org URL with BleepingComputer for a text file hosted on the "login.us2.oraclecloud.com" server that contained their email address. This file indicates that the threat actor could create files on Oracle's server, indicating an actual breach.
However, Oracle has denied that it suffered a breach of Oracle Cloud and has refused to respond to any further questions about the incident.
"There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data," the company told BleepingComputer last Friday.
This denial, however, contradicts findings from BleepingComputer, which received additional samples of the leaked data from the threat actor and contacted the associated companies.
Representatives from these companies, all who agreed to confirm the data under the promise of anonymity, confirmed the authenticity of the information. The companies stated that the associated LDAP display names, email addresses, given names, and other identifying information were all correct and belonged to them.
The threat actor also shared emails with BleepingComputer, claiming to be part of an exchange between them and Oracle.
One email shows the threat actor contacting Oracle's security email (secalert_us@oracle.com) to report that they hacked the servers.
"I've dug into your cloud dashboard infrastructure and found a massive vulnerability that has handed me full access to info on 6 million users," reads the email seen by BleepingComputer.
Another email thread shared with BleepingComputer shows an exchange between the threat actor and someone using a ProtonMail email address who claims to be from Oracle. BleepingComputer has redacted the email address of this other person as we could not verify their identity or the veracity of the email thread.
In this email exchange, the threat actor says someone from Oracle using a @proton.me email address told them that "We received your emails. Let’s use this email for all communications from now on. Let me know when you get this."
Cybersecurity firm Cloudsek has also found an Archive.org URL showing that the "login.us2.oraclecloud.com" server was running Oracle Fusion Middleware 11g as of February 17, 2025. Oracle has since taken this server offline after news of the alleged breach was reported.
This version of the software was impacted by a vulnerability tracked as CVE-2021-35587 that allowed unauthenticated attackers to compromise Oracle Access Manager. The threat actor claimed that this vulnerability was used in the alleged breach of Oracle's servers.
BleepingComputer has emailed Oracle numerous times about this information but has not received any response.
Source: https://www.bleepingcomputer.com/ne...data-stolen-in-alleged-cloud-breach-is-valid/
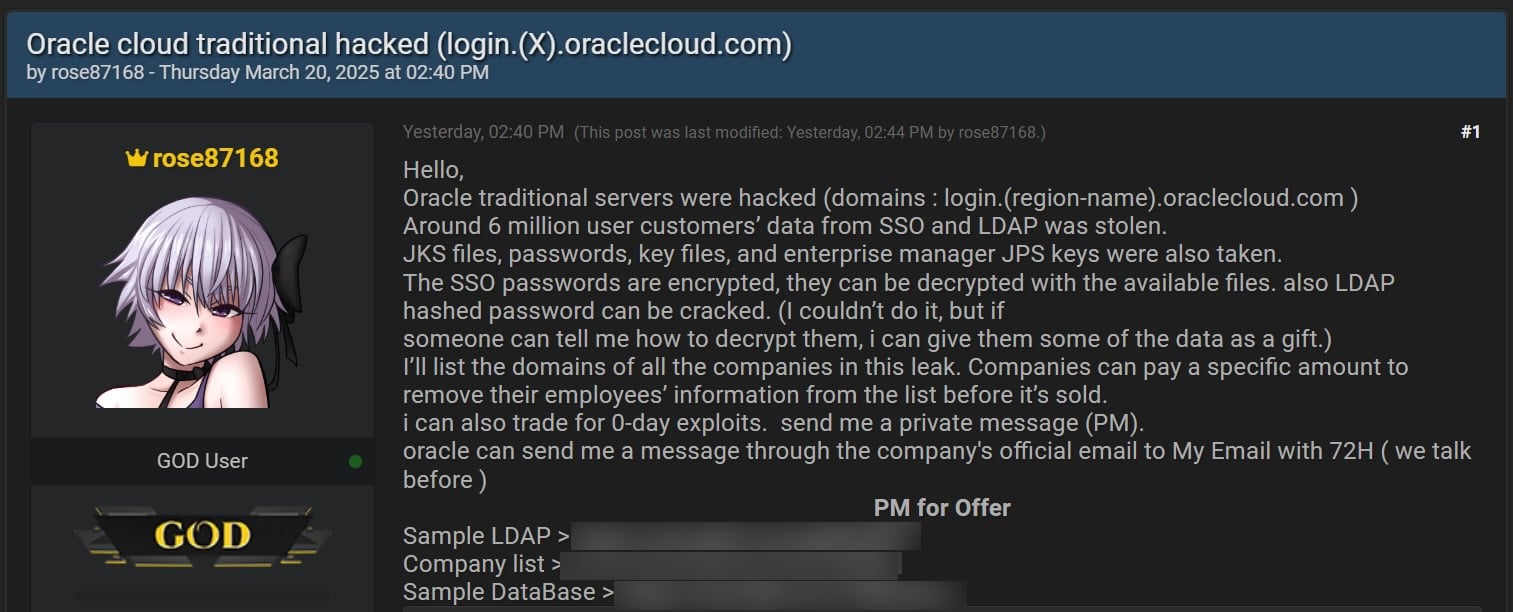
Last week, a person named ‘rose87168’ claimed to have breached Oracle Cloud servers and began selling the alleged authentication data and encrypted passwords of 6 million users. The threat actor also said that stolen SSO and LDAP passwords could be decrypted using the info in the stolen files and offered to share some of the data with anyone who could help recover them.
The threat actor released multiple text files consisting of a database, LDAP data, and a list of 140,621 domains for companies and government agencies that were allegedly impacted by the breach. It should be noted that some of the company domains look like tests, and there are multiple domains per company.

Source: BleepingComputer
In addition to the data, rose87168 shared an Archive.org URL with BleepingComputer for a text file hosted on the "login.us2.oraclecloud.com" server that contained their email address. This file indicates that the threat actor could create files on Oracle's server, indicating an actual breach.
However, Oracle has denied that it suffered a breach of Oracle Cloud and has refused to respond to any further questions about the incident.
"There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data," the company told BleepingComputer last Friday.
This denial, however, contradicts findings from BleepingComputer, which received additional samples of the leaked data from the threat actor and contacted the associated companies.
Representatives from these companies, all who agreed to confirm the data under the promise of anonymity, confirmed the authenticity of the information. The companies stated that the associated LDAP display names, email addresses, given names, and other identifying information were all correct and belonged to them.
The threat actor also shared emails with BleepingComputer, claiming to be part of an exchange between them and Oracle.
One email shows the threat actor contacting Oracle's security email (secalert_us@oracle.com) to report that they hacked the servers.
"I've dug into your cloud dashboard infrastructure and found a massive vulnerability that has handed me full access to info on 6 million users," reads the email seen by BleepingComputer.
Another email thread shared with BleepingComputer shows an exchange between the threat actor and someone using a ProtonMail email address who claims to be from Oracle. BleepingComputer has redacted the email address of this other person as we could not verify their identity or the veracity of the email thread.
In this email exchange, the threat actor says someone from Oracle using a @proton.me email address told them that "We received your emails. Let’s use this email for all communications from now on. Let me know when you get this."
Cybersecurity firm Cloudsek has also found an Archive.org URL showing that the "login.us2.oraclecloud.com" server was running Oracle Fusion Middleware 11g as of February 17, 2025. Oracle has since taken this server offline after news of the alleged breach was reported.
This version of the software was impacted by a vulnerability tracked as CVE-2021-35587 that allowed unauthenticated attackers to compromise Oracle Access Manager. The threat actor claimed that this vulnerability was used in the alleged breach of Oracle's servers.
BleepingComputer has emailed Oracle numerous times about this information but has not received any response.
Source: https://www.bleepingcomputer.com/ne...data-stolen-in-alleged-cloud-breach-is-valid/